Managed Security Services
Centralpoint can be installed On Premise (within the Client's network, even behind the firewall), on a Dedicated (Physical) Hosting service, or in the Cloud (Virtual public or private cloud). Approximately 50% of our client base choose to host themselves either on premise or with a hosting provider of their choice. In the event that you are interested in having Oxcyon provide hosting services for you, we depend on our strategic alliance partner, Rackspace to provide these services. Racksapce shares the same Lifecycle Management philosophy as Oxcyon, wherein they expect change, and are able to rapidly respond to it.
In the event you seek our hosting services, Compliance (or security) is of utmost concern, and feel that Rackspace has the right Security Lifecycle in place. Like Oxcyon's bi weekly, evergreen updates, security and compliance is changing all the time. Oxcyon needs a vendor who is committed to change with it.. Oxcyon provides additional reporting and forensics (from the (Centralpoint) application layer, which are mashed up and compared within the network (and security) tracked by Rackspace. This video, by Rackspace's Chief Security Officer, Brian Kelly shares our kindred value of lifecycles, updates, and a commitment toward 'anticipating surprise'. Learn more about Oxcyon's Security Incident Policy and our steps to maintain your compliance. This partnership allows a two prong approach to the maintenance of your environment, so that both Oxcyon and Rackspace can 'listen' to your project. This listening includes both Network Security, Hardware and even Application monitoring by both Oxcyon and Rackspace, so that you can receive a consolidated report of ALL activity to report on all activity to your site or project.
Real Time Alerts & Reporting
Security monitoring can involve both data from the hosting provider Oxcyon depending on the level of service you have. These reports can include a mash up of both environmental and application activity for a full forensic analysis regarding any site activity or anomalies.
- RACKSPACE MONITORING
- Performance Activity (Server, Memory, CPU, Load)
- Network Monitoring (All activity)
- IP Activity, Blocking
- DOS Attempts & Block
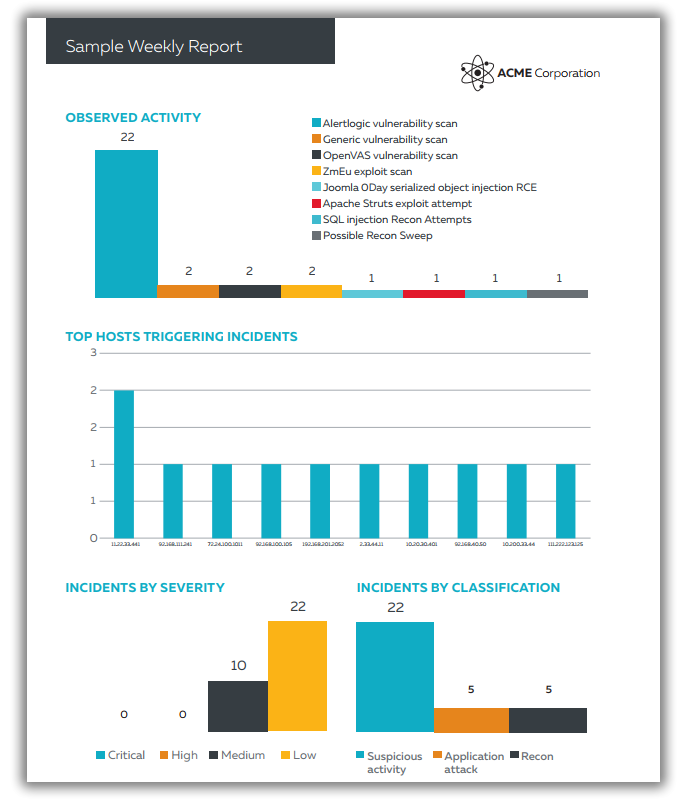
- Top Hosts Triggering Incidents
- Incidents by Severity
- Incidents by Classification
- Threat Landscape Assessments
- Vulnerability Reporting
- Vulnerability Detail(s)
OXCYON MONITORING
- Exception Monitoring (EKC) Any Application Anomalies
- IP Activity, Blocking (Application Layer)
- Performance Log
- Cross Site Scripting Attempts
- Database Injection (SQL) Attempts
- Malware Upload Attempts
- DOS (Denial of Service Attempts)
- Advertising Tracking
- Failed Data Connections (Authentication, Database (Data Transfer) or via WebAPI)
- Usability (Content Management & Gamification)
- Site Traffic Analytics (Google & Others)
|
Download Report Example
|